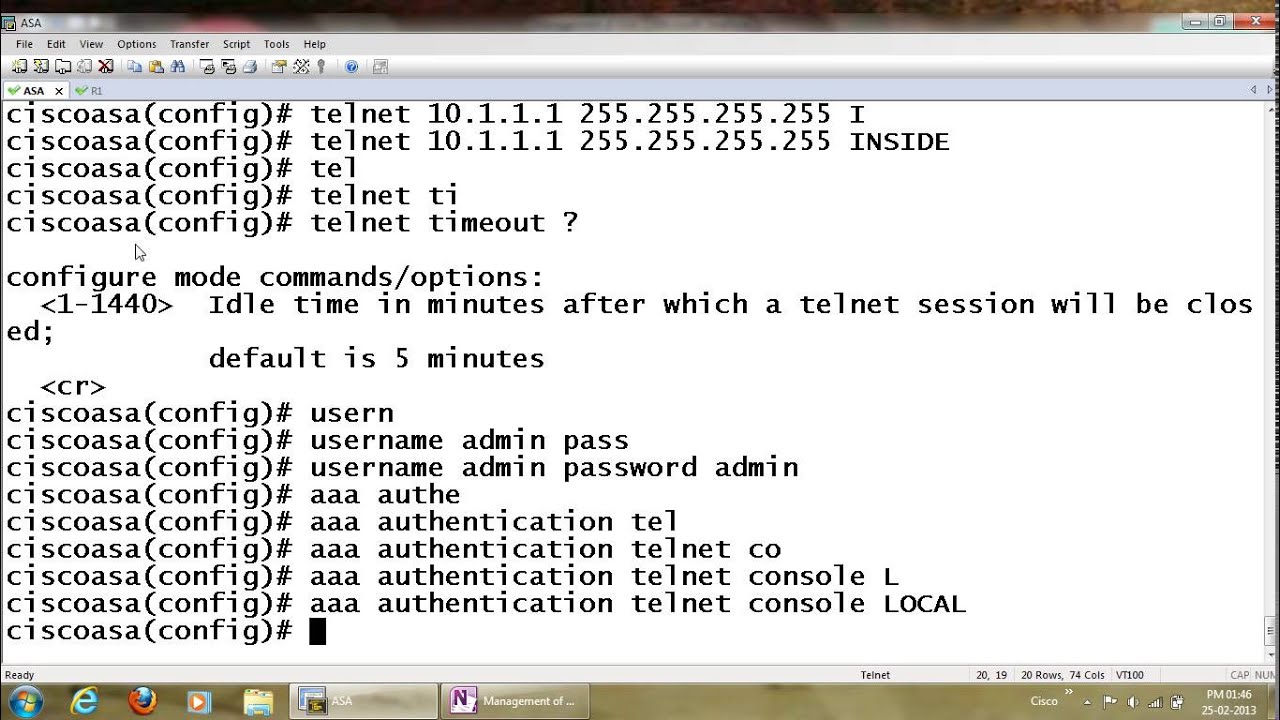
Several types of passwords can be configured on a Cisco router, such as the enable password, the secret password for Telnet and SSH connections and the console port as well. All these password locations represent good access locations for passwords, but if you have only one password on only one access location, you should at least have an. R1(config-line)#transport input telnet. The router will now accept telnet connections but without authentication, it’s not going to work. Let’s configure a password: R1(config-line)#password mypassword R1(config-line)#login. The password will be “mypassword”. The login command tells the router to check for this password. Transport input telnet ssh. Access-class 23 in. Privilege level 15. Transport input telnet ssh! Scheduler allocate! Saved the config & reload the router but still the same issue. Regards, Mahesh. † Viewing Console Port, SSH, and Telnet Handling Configurations, page 4-11 † Important Notes and Restrictions, page 4-16 Console Port Overview for the Cisco ASR 1000 Series Routers The console port on the Cisco ASR 1000 Series Router is an EIA/TIA-232 asynchronous, serial connection with no flow control and an RJ-45 connector.
If you have a Synology NAS and had some sort of disk crash in the past, you've probably encountered the famous 'Cannot format system partition' and 'Please configure your router to forward port 23 to DiskStation and contact Synology online support'.
Yeah, it sucks.
It sucks even more when you know the disk is perfectly fine, and you still have hopes to recover your data. Or you simply don't like the idea of having your port 23 open to the world for god-knows-how-long until a Synology tech support can look into your case.
You've probably tried telneting to your NAS. Maybe you've even tried opening the case and hacking the serial port, only to discover that you don't have the root password. The DS Assistant password doesn't work, and you exhausted all obvious guesses - blank, synopass, synology, password, admin, root, etc.
Well, what about c12-0804? No, I didn't make this up. This is today's password.
But if you're reading this a few days (or years) from now, too bad; it won't work. Unless, of course, you wait until December 8th. Because the password repeats every year.
Basically Synology hardcoded a modified login binary within the firmware that accepts an obfuscated password for root, which depends on the current date. (by the way, this isn't the only thing Synology folks hardcoded in the firmware).
Thanks to GPL, Synology was forced to publish the original source code for the firmware. Based on the original correct_password.c code, I hacked a short snippet to generate the daily password.
Here's the Synology Telnet password generator:
Compile and run the code above with gcc. You can also use the excellent CodepadRepl.it to run the code online and get the password for today (no registration needed).
Bonus tip: if you're curious how exactly the password is generated, here's the algorithm:

- 1st character = month in hexadecimal, lower case (1=Jan, ... , a=Oct, b=Nov, c=Dec)
- 2-3 = month in decimal, zero padded and starting in 1 (01, 02, 03, ..., 11, 12)
- 4 = dash
- 5-6 = day of the month in hex (01, 02 .., 0A, .., 1F)
- 7-8 = greatest common divisor between month and day, zero padded. This is always a number between 01 and 12.
So, let's say today is October 15, the password would be: a10-0f05 where a = month in hex, 10 = month in decimal, 0f = day in hex, 05 = greatest divisor between 10 and 15).
If you have trouble calculating the greatest common divisor (elementary math, anyone?), Wolfram Alpha is your friend.
This was tested on a Synology DS212+, with Marvell Kirkwood mv6282 chipset. It's unlikely but still possible that different models use a different algorithm. YMMV, so always check the source code.
[UPDATE 1: Several users reported that this works in many other models, including DS409, DS112j, etc. Please leave a comment with your model and firmware version.]
[UPDATE 2: If it doesn't work, it's probably that your date is incorrect in the NAS. Per Patrick's suggestion below, try '101-0101', which is the password for Jan 01]
Cisco Line VTY (Virtual terminal line):
VTY is short for Virtual Terminal lines and are used for accessing the router remotely through telnet by using these virtual router interfaces.The number of Cisco vty lines is not consistent in all routers, but different cisco routers/switches can have different number of vty lines. The more vty lines a router or switch has the more users can access that device simultaneously through telnet.
You should also learn about encrypted enable mode password or enable secret cisco password.
Checking the number of Cisco VTY lines:
The number of vty lines determine the number of simultaneous telnet connections we can have to that specific cisco router/switch. From security perspective it is extremely important to know the number of virtual lines your router / switch has, and these vty lines must be secured by a password to prevent unauthorized telnet access.
Although it is not a requirement of setting vty line password, but generally a good practice to secure console line, enable mode and auxiliary line by setting a password for each. Read more about console line password, enable password, auxiliary line password and enable secret password.
When you are at global configuration mode type line vty ? this command will display the number of vty lines or interfaces your router has.
Setting line VTY / TELNET Password:
For setting a password for VTY lines you should be at the global configuration mode. As we have 16 interfaces/lines ranging from 0-15 and we will specify a single password for all these, in order to secure our router. 16 interfaces/lines means that we can have 16 simultaneous telnet (remote) connections to this router.
When at global configuration mode type line vty 0 15 for entering vty line configuration mode.
Hack Cisco Router Password Telnet Port Settings
Command syntax:line vty starting-interface ending-interface-range
How to remove cisco line vty password:
In cisco removing or undoing a settings is very easy, just type no before the command which you used for making changes. For removing vty line password go to the global configuration mode than to line configuration mode and than type no password. For adding extra security to a router you should also read How Set Line Console password, How to set auxiliary line password and how to set enable secret password on cisco router.
When you press enter the line vty cisco password will be disabled. Now that you have learned how to set line vty password and how to remove vty password(Telnet Password), you may want to learn How to Telnet a Cisco Router.